- Generate Triple Des Key
- Triple Des Encryption Key Generator Free
- Triple Des Encryption Key Generator Reviews
- Cryptography Tutorial
- Cryptography Useful Resources
- Selected Reading
The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST).
DES is an implementation of a Feistel Cipher. It uses 16 round Feistel structure. The block size is 64-bit. Though, key length is 64-bit, DES has an effective key length of 56 bits, since 8 of the 64 bits of the key are not used by the encryption algorithm (function as check bits only). General Structure of DES is depicted in the following illustration −
Generate Triple Des Key
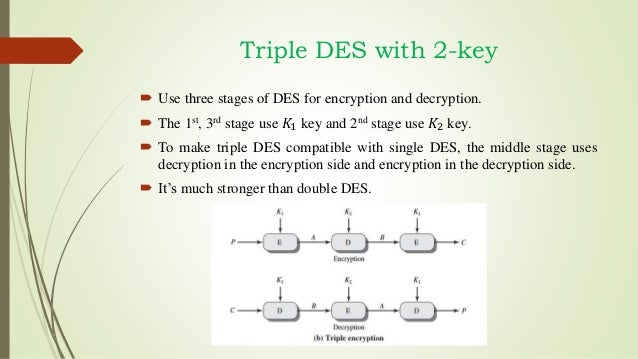
In cryptography, Triple DES (3DES or TDES), officially the Triple Data Encryption Algorithm (TDEA or Triple DEA), is a symmetric-key block cipher, which applies the DES cipher algorithm three times to each data block. The Data Encryption Standard's (DES) 56-bit key is no longer considered adequate in the face of modern cryptanalytic techniques. If you want a managed service for creating and controlling your encryption keys, but you don't want or need to operate your own HSM, consider using AWS Key Management Service. To learn more about what you can do with AWS CloudHSM, see the following topics.
Since DES is based on the Feistel Cipher, all that is required to specify DES is −
- Round function
- Key schedule
- Any additional processing − Initial and final permutation
Jul 28, 2017 Synopsis Triple Data Encryption Algorithm (3DES) is an advancement of the popular DES standard. 3DES utilizes symmetric key block cipher. Using three unrelated 64 bit keys, 3DES was created to encrypt 64 bit blocks of data. In DES block, each key is utilized as an input. Without creating an entire.
Initial and Final Permutation
The initial and final permutations are straight Permutation boxes (P-boxes) that are inverses of each other. They have no cryptography significance in DES. The initial and final permutations are shown as follows −
Round Function
The heart of this cipher is the DES function, f. The DES function applies a 48-bit key to the rightmost 32 bits to produce a 32-bit output.
-
Expansion Permutation Box − Since right input is 32-bit and round key is a 48-bit, we first need to expand right input to 48 bits. Permutation logic is graphically depicted in the following illustration −
-
The graphically depicted permutation logic is generally described as table in DES specification illustrated as shown −
-
XOR (Whitener). − After the expansion permutation, DES does XOR operation on the expanded right section and the round key. The round key is used only in this operation.
-
Substitution Boxes. − The S-boxes carry out the real mixing (confusion). DES uses 8 S-boxes, each with a 6-bit input and a 4-bit output. Refer the following illustration −
-
The S-box rule is illustrated below −
-
There are a total of eight S-box tables. The output of all eight s-boxes is then combined in to 32 bit section.
-
Straight Permutation − The 32 bit output of S-boxes is then subjected to the straight permutation with rule shown in the following illustration:
Key Generation
The round-key generator creates sixteen 48-bit keys out of a 56-bit cipher key. The process of key generation is depicted in the following illustration −
The logic for Parity drop, shifting, and Compression P-box is given in the DES description.
DES Analysis
The DES satisfies both the desired properties of block cipher. These two properties make cipher very strong.
-
Avalanche effect − A small change in plaintext results in the very great change in the ciphertext.
-
Completeness − Each bit of ciphertext depends on many bits of plaintext.
During the last few years, cryptanalysis have found some weaknesses in DES when key selected are weak keys. These keys shall be avoided.
DES has proved to be a very well designed block cipher. There have been no significant cryptanalytic attacks on DES other than exhaustive key search.
-->
Definition
Represents the base class for Triple Data Encryption Standard algorithms from which all TripleDES implementations must derive.
Inheritance
- Derived
- Attributes
Examples
The following code example method uses TripleDESCryptoServiceProvider with the specified key (Key) and initialization vector (IV) to encrypt a file specified by inName. It then outputs the encrypted result to the file specified by outName.
Decryption can be handled in the same way; use CreateDecryptor instead of CreateEncryptor. The same key (Key) and initialization vector (IV) used to encrypt the file must be used to decrypt it.
Remarks
TripleDES uses three successive iterations of the DES algorithm. It can use either two or three 56-bit keys.
Triple Des Encryption Key Generator Free
Note
A newer symmetric encryption algorithm, Advanced Encryption Standard (AES), is available. Consider using the Aes class and its derived classes instead of the TripleDES class. Use TripleDES only for compatibility with legacy applications and data.
This algorithm supports key lengths from 128 bits to 192 bits in increments of 64 bits.
Constructors
| TripleDES() |
Initializes a new instance of the TripleDES class. |
Fields
Triple Des Encryption Key Generator Reviews
| BlockSizeValue |
Represents the block size, in bits, of the cryptographic operation. (Inherited from SymmetricAlgorithm) |
| FeedbackSizeValue |
Represents the feedback size, in bits, of the cryptographic operation. (Inherited from SymmetricAlgorithm) |
| IVValue |
Represents the initialization vector (IV) for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| KeySizeValue |
Represents the size, in bits, of the secret key used by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| KeyValue |
Represents the secret key for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| LegalBlockSizesValue |
Specifies the block sizes, in bits, that are supported by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| LegalKeySizesValue |
Specifies the key sizes, in bits, that are supported by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| ModeValue |
Represents the cipher mode used in the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| PaddingValue |
Represents the padding mode used in the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
Properties
| BlockSize |
Gets or sets the block size, in bits, of the cryptographic operation. (Inherited from SymmetricAlgorithm) |
| FeedbackSize |
Gets or sets the feedback size, in bits, of the cryptographic operation for the Cipher Feedback (CFB) and Output Feedback (OFB) cipher modes. (Inherited from SymmetricAlgorithm) |
| IV |
Gets or sets the initialization vector (IV) for the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| Key |
Gets or sets the secret key for the TripleDES algorithm. |
| KeySize |
Gets or sets the size, in bits, of the secret key used by the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| LegalBlockSizes |
Gets the block sizes, in bits, that are supported by the symmetric algorithm. |
| LegalKeySizes |
Gets the key sizes, in bits, that are supported by the symmetric algorithm. |
| Mode |
Gets or sets the mode for operation of the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
| Padding |
Gets or sets the padding mode used in the symmetric algorithm. (Inherited from SymmetricAlgorithm) |
Methods
| Clear() |
Releases all resources used by the SymmetricAlgorithm class. (Inherited from SymmetricAlgorithm) |
| Create() |
Creates an instance of a cryptographic object to perform the TripleDES algorithm. |
| Create(String) |
Creates an instance of a cryptographic object to perform the specified implementation of the TripleDES algorithm. |
| CreateDecryptor() |
Creates a symmetric decryptor object with the current Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| CreateDecryptor(Byte[], Byte[]) |
When overridden in a derived class, creates a symmetric decryptor object with the specified Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| CreateEncryptor() |
Creates a symmetric encryptor object with the current Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| CreateEncryptor(Byte[], Byte[]) |
When overridden in a derived class, creates a symmetric encryptor object with the specified Key property and initialization vector (IV). (Inherited from SymmetricAlgorithm) |
| Dispose() |
Releases all resources used by the current instance of the SymmetricAlgorithm class. (Inherited from SymmetricAlgorithm) |
| Dispose(Boolean) |
Releases the unmanaged resources used by the SymmetricAlgorithm and optionally releases the managed resources. (Inherited from SymmetricAlgorithm) |
| Equals(Object) |
Determines whether the specified object is equal to the current object. (Inherited from Object) |
| GenerateIV() |
Bioshock infinite key generator download. When overridden in a derived class, generates a random initialization vector (IV) to use for the algorithm. (Inherited from SymmetricAlgorithm) |
| GenerateKey() |
When overridden in a derived class, generates a random key (Key) to use for the algorithm. (Inherited from SymmetricAlgorithm) |
| GetHashCode() |
Serves as the default hash function. (Inherited from Object) |
| GetType() |
Gets the Type of the current instance. (Inherited from Object) |
| IsWeakKey(Byte[]) |
Determines whether the specified key is weak. |
| MemberwiseClone() |
Creates a shallow copy of the current Object. (Inherited from Object) |
| ToString() |
Returns a string that represents the current object. (Inherited from Object) |
| ValidKeySize(Int32) |
Determines whether the specified key size is valid for the current algorithm. (Inherited from SymmetricAlgorithm) |
Explicit Interface Implementations
| IDisposable.Dispose() |
Releases the unmanaged resources used by the SymmetricAlgorithm and optionally releases the managed resources. (Inherited from SymmetricAlgorithm) |